
Unknown attackers target Russian entities with newly discovered malware that allows them to control and steal information from compromised devices remotely.
According to Malwarebytes, one of the Russian organizations that were attacked using this malware is a government-controlled defense corporation.
"Based on a fake domain registered by the threat actors, we know that they tried to target a Russian aerospace and defense entity known as OAK," the Malwarebytes Labs researchers said.
Dubbed Woody RAT, this remote access trojan (RAT) has a wide range of capabilities and has been used in attacks for at least one year.
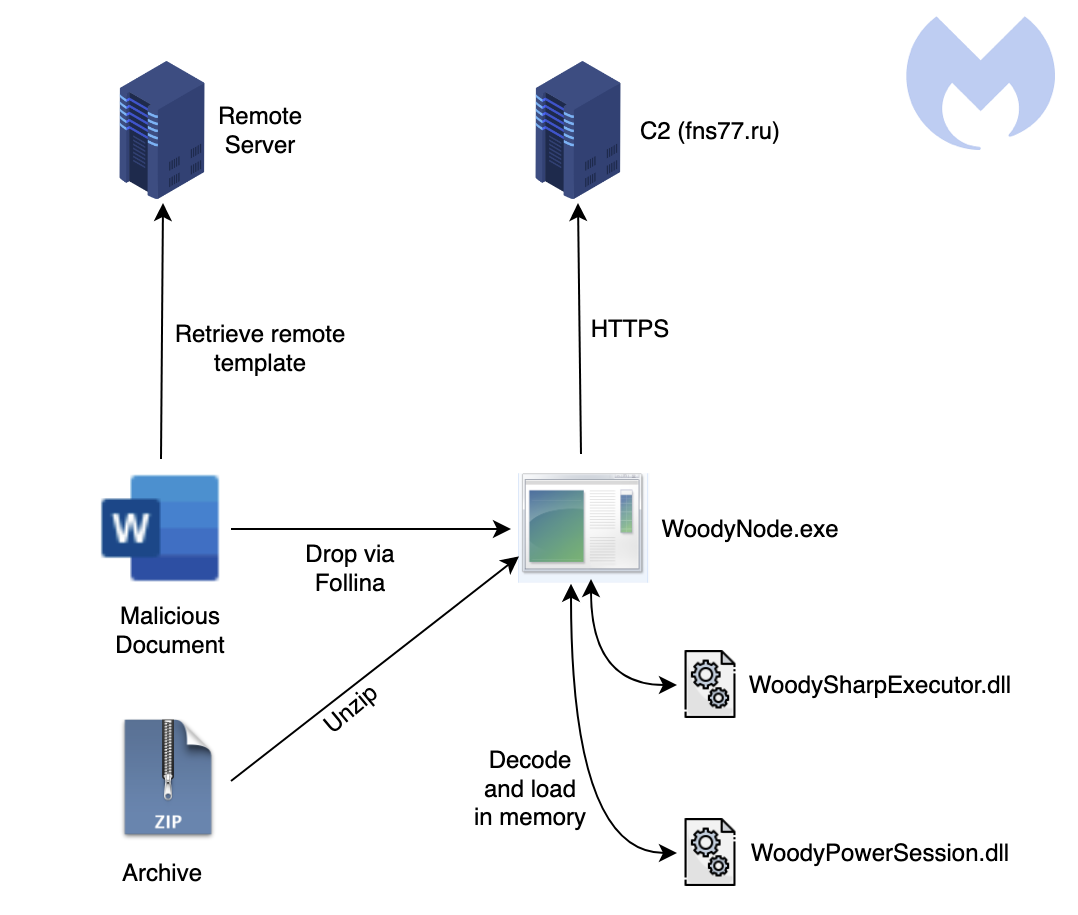
This malware is currently delivered onto targets' computers via phishing emails through two distribution methods: ZIP archive files containing the malicious payload or "Information security memo" Microsoft Office documents that exploit the Follina vulnerability to drop the payloads.
"The earliest versions of this Rat was typically archived into a zip file pretending to be a document specific to a Russian group," the researchers added.
"When the Follina vulnerability became known to the world, the threat actor switched to it to distribute the payload, as identified by MalwareHunterTeam."
Its list of features includes collecting system information, listing folders and running processes, executing commands and files received from its command-and-control (C2) server, downloading, uploading, and deleting files on infected machines, and taking screenshots.
Woody RAT can also execute .NET code and PowerShell commands and scripts received from its C2 server using two DLLs named WoodySharpExecutor and WoodyPowerSession.
Once launched on a compromised device, the malware uses process hollowing to inject itself into a suspended Notepad process, deletes itself from the disk to evade detection from security products, and resumes the thread.
The RAT encrypts its C2 communication channels using a combination of RSA-4096 and AES-CBC to elude network-based monitoring.
Malwarebytes is yet to attribute the malware and the attacks to a known threat group but said that a very short list of possible suspects includes Chinese and North Korean APTs.
"This very capable Rat falls into the category of unknown threat actors we track. Historically, Chinese APTs such as Tonto team as well as North Korea with Konni have targeted Russia," the researchers concluded.
"However, based on what we were able to collect, there weren't any solid indicators to attribute this campaign to a specific threat actor."
This aligns with recent findings from several other vendors who also spotted Chinese hacking groups targeting Russian officials, government agencies and entities, and aerospace firms.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now